SANS Holiday Hack Challenge 2025 - Intro to nmap
A beginner-friendly challenge teaching the fundamentals of nmap network scanning, including basic scans, full port scans, IP range scanning, service version detection, and using ncat for connections.
The Challenge
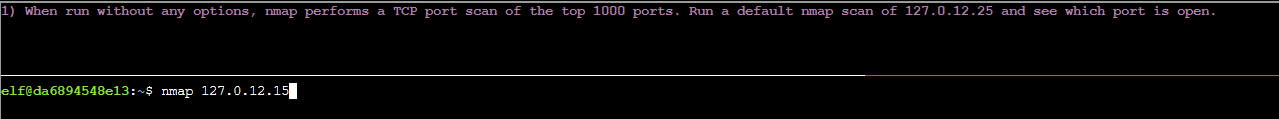
Initially we are told to run a simple flag-less scan of the IP 127.0.12.25, which can be done by simply running nmap 127.0.12.25
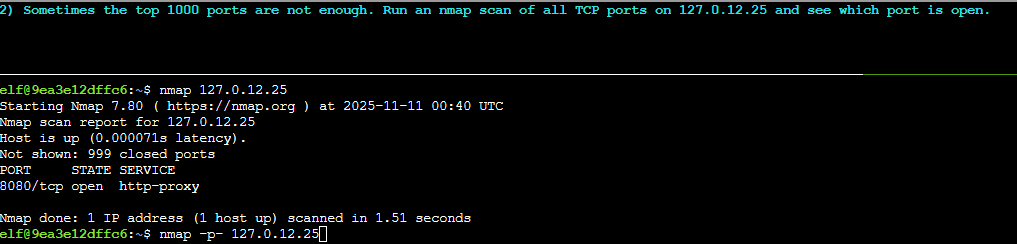
This reveals port 8080 to be open, but they now want us to scan all tcp ports, which can be done by adding the -p- flag.
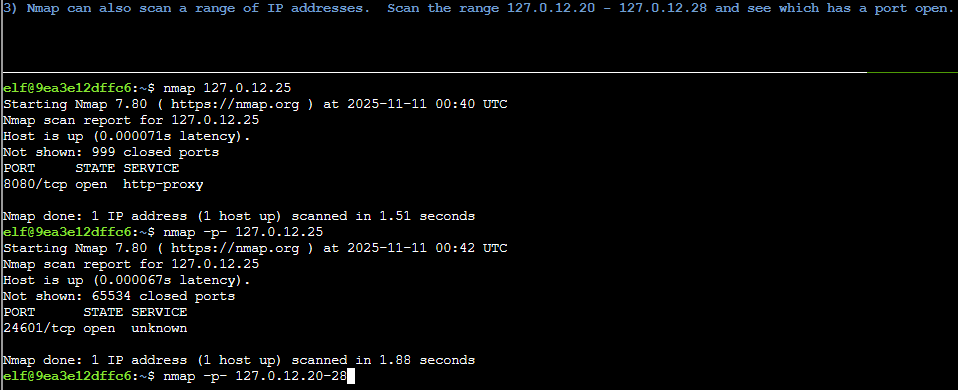
Doing so we find an unknown service on port 24601. Next they want us to scan a range of ip addresses from 127.0.12.20 to 127.0.12.28, which we can do by setting the ip parameter to 127.0.12.20-28.
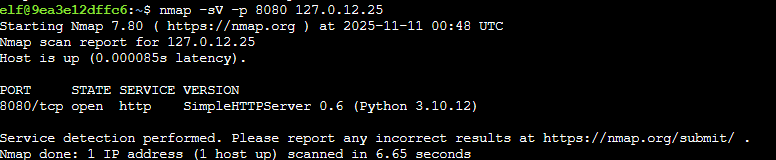
Doing so we find a few different open ports. Next they want us to find the specific version of the service running on port 8080 of 127.0.12.25. We can do this by adding the -sV flag, making our command nmap -sV -p 8080 127.0.12.25
As seen in the screenshot above it is a simple HTTP server running on python. We are now asked to connect to the port 24601 on the IP 127.0.12.25, which can be done with the command ncat 127.0.12.25 24601 using the ncat tool built into nmap.
After getting the connection we get the message that the challenge is completed!