Holiday Hack Challenge 2025 - The Open Door
A cloud security audit challenge identifying dangerous firewall misconfigurations in Azure Network Security Groups that expose production systems to internet-based attacks.
Solving the challenge
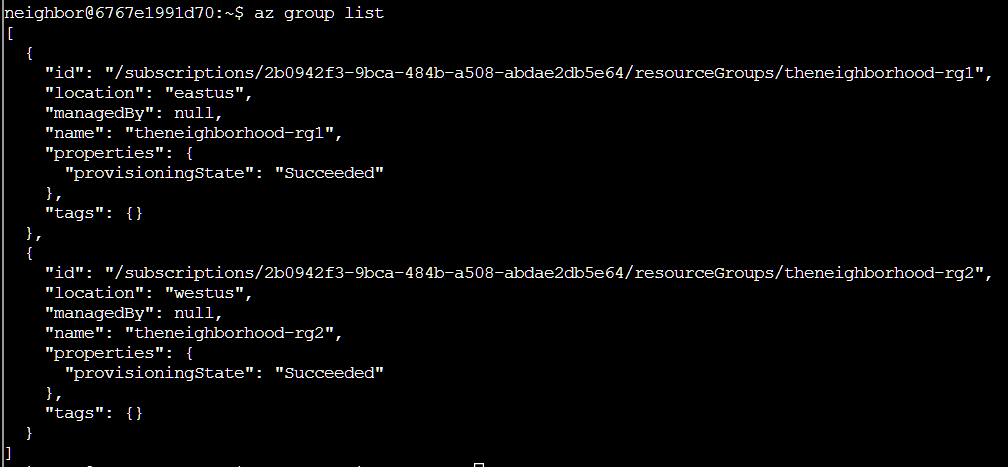
As usual we are given a bit of a walkthrough at the start of these act one challenges, and are told to run the command az group list
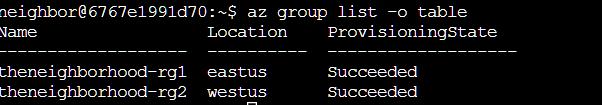
This outputs the group list in JSON format, so I ran az group list -o table to view it in a table format. This shows us the resource groups in the Azure environment, which are logical containers that hold related Azure resources.
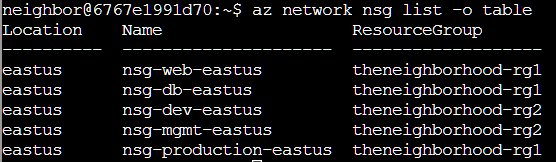
Next we were told to view all the Network Security Groups (NSGs), which we can do with az network nsg list -o table. NSGs are Azure’s firewall rules that control inbound and outbound network traffic to Azure resources. Each NSG contains security rules that allow or deny traffic based on source, destination, port, and protocol.
This showed 5 NSGs, 3 for rg1 and two for rg2. We were then instructed to check the “Web” NSG, which I did using the az network nsg show --name nsg-web-eastus --resource-group theneighborhood-rg1 | less command. The | less pipe allows us to page through the full JSON output of the NSG configuration.
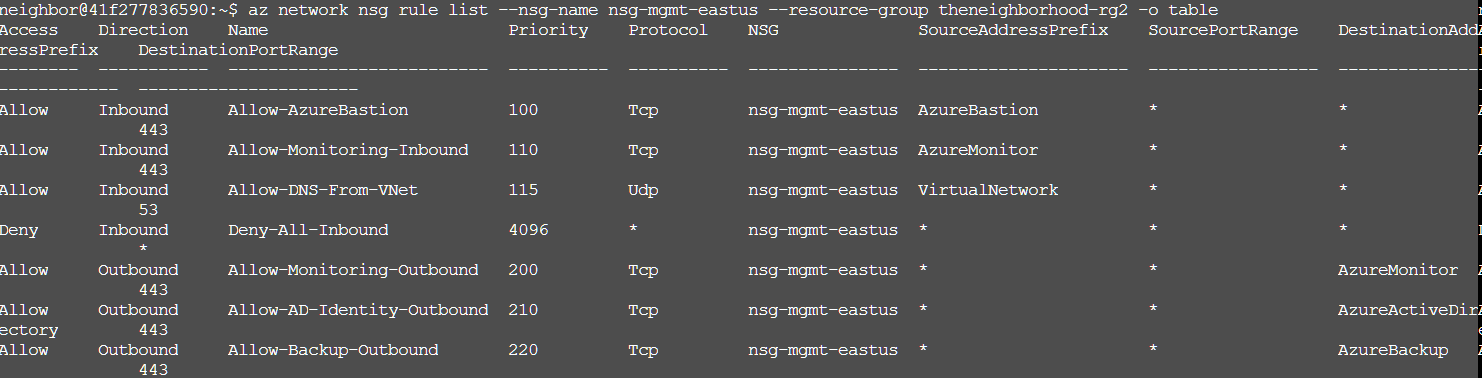
After doing so we were told to do the same with the mgmt NSG, but to focus on viewing the rules, which we could do with az network nsg rule list --nsg-name nsg-mgmt-eastus --resource-group theneighborhood-rg2 -o table. This command specifically lists just the security rules in a table format for easier analysis.
The management NSG appeared properly configured. It only allowed inbound traffic from Azure services (AzureBastion, AzureMonitor, VirtualNetwork) rather than from the public internet, and had a deny-all rule as a catch-all at the end.
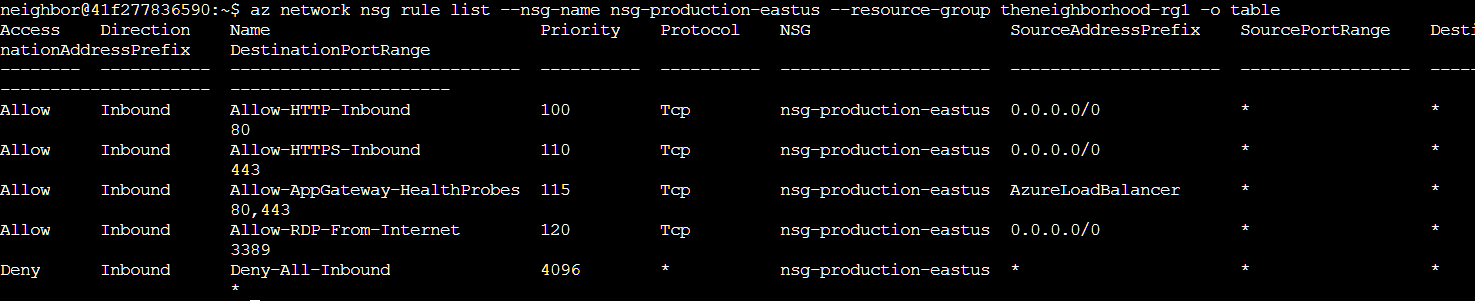
Everything seemed in order, however we were told there is a suspect rule somewhere in the NSGs that needed to be found. After enumerating the “production” NSG with az network nsg rule list --nsg-name nsg-production-eastus --resource-group theneighborhood-rg1 -o table, I found something interesting.
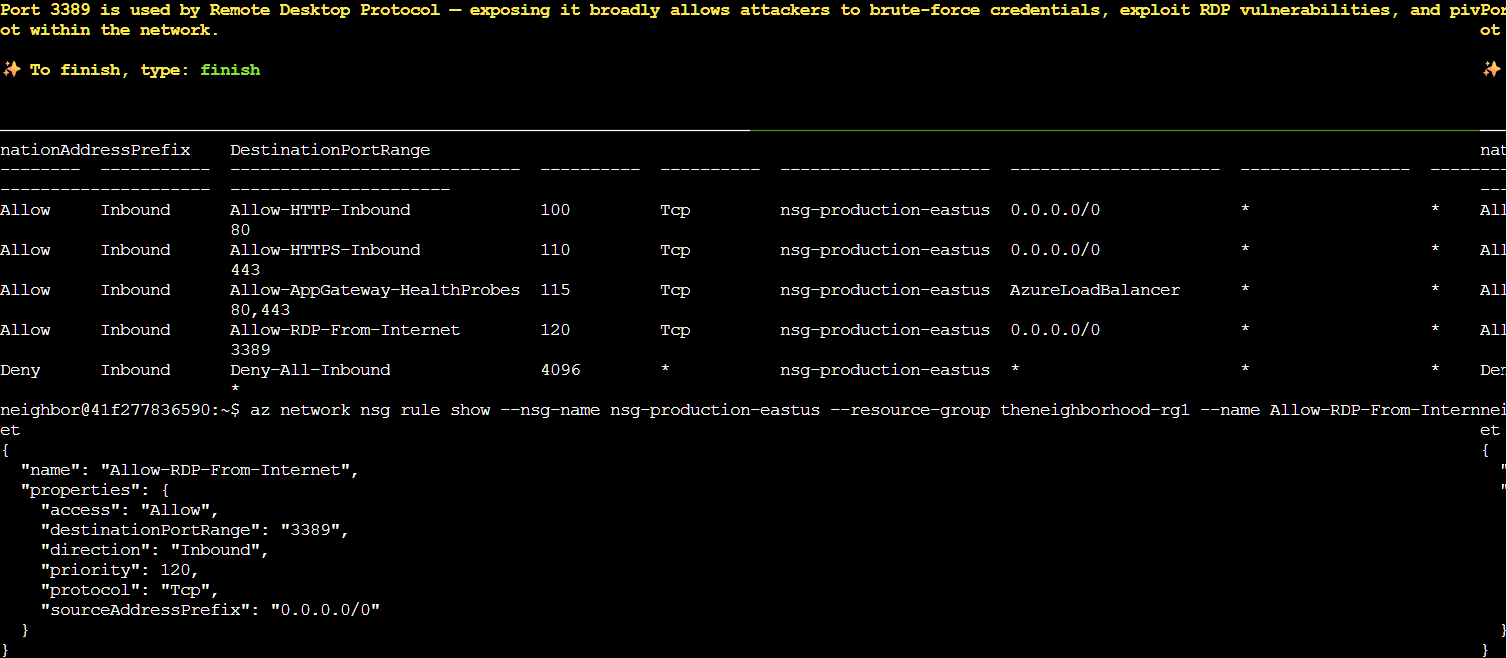
The third rule on the list, “Allow-RDP-From-Internet” is extremely dangerous. It’s allowing RDP (Remote Desktop Protocol) access from anywhere on the internet (0.0.0.0/0 means any source IP address) to production systems on port 3389. This is a critical security vulnerability as RDP provides direct system-level access and should never be exposed to the public internet. It’s a common target for brute force attacks and automated exploitation attempts. RDP access should be restricted to specific trusted IP addresses or accessed through secure channels like Azure Bastion or VPN. To take a closer look at the rule I ran az network nsg rule show --nsg-name nsg-production-eastus --resource-group theneighborhood-rg1 --name Allow-RDP-From-Internet
This was in fact the rule we were looking for. The rule details confirm it has "access": "Allow", "direction": "Inbound", "sourceAddressPrefix": "0.0.0.0/0", and "destinationPortRange": "3389". This is a textbook example of an overly permissive NSG rule that exposes production infrastructure to internet-based attacks.
Now all that was needed was to simply type finish to complete the challenge.