Advent of Cyber 2025 - Day 11 - Merry XSSMas Triage
Day 11 of Advent of Cyber 2025 exploring Cross-Site Scripting (XSS) vulnerabilities by identifying and exploiting both Reflected and Stored XSS attacks on McSkidy's message portal.
Description
After last year’s automation and tech modernisation, Santa’s workshop got a new makeover. McSkidy has a secure message portal where you can contact her directly with any questions or concerns. However, lately, the logs have been lighting up with unusual activity, ranging from odd messages to suspicious search terms. Even Santa’s letters appear to be scripts or random code. Your mission, should you choose to accept it: dig through the logs, uncover the mischief, and figure out who’s trying to mess with McSkidy.
Learning Objectives:
- Understand how XSS works
- Learn to prevent XSS attacks
Introduction
This is the eleventh challenge in this year’s Advent of Cyber hosted by TryHackMe, a 24 day cyber security challenge where new objectives are released every day. Each objective consists of multiple questions and flags we must find on their machines, sometimes by simply following their instructions and other times by needing to find something hidden ourselves. This challenge focuses on Cross-Site Scripting (XSS) vulnerabilities, specifically Reflected XSS and Stored XSS. We’ll be investigating unusual activity on McSkidy’s secure message portal, where logs have been lighting up with suspicious search terms and messages that appear to contain malicious scripts. As usual we begin by launching the target machine and either connecting to it via VPN or using their in browser attack box, which I will be doing.
Solving the Challenge
Which type of XSS attack requires payloads to be persisted on the backend?
Answer: Stored
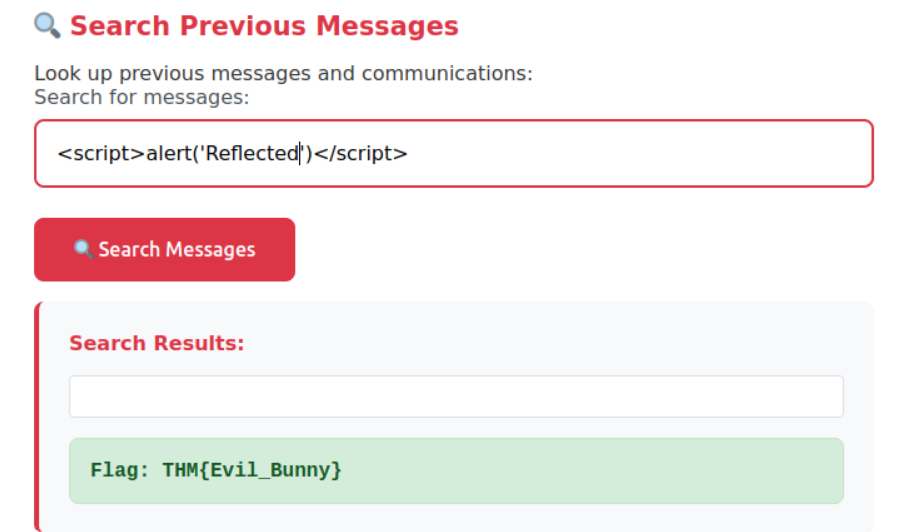
What’s the reflected XSS flag?
In order to find this we need to visit the website hosted on the machine. Once there we can see a search bar which is vulnerable to XSS. By entering the payload <script>alert('TEXT HERE')</script> we can make the website process the code as executable JavaScript rather than plain text, which makes it pop up an alert. After clearing the alert, the flag will be right there on the screen.
The key characteristic of Reflected XSS is that the malicious script is immediately reflected back in the response and executed, but it’s not stored on the server. This type of attack typically requires tricking a victim into clicking a malicious link containing the payload.
Answer: THM{Evil_Bunny}
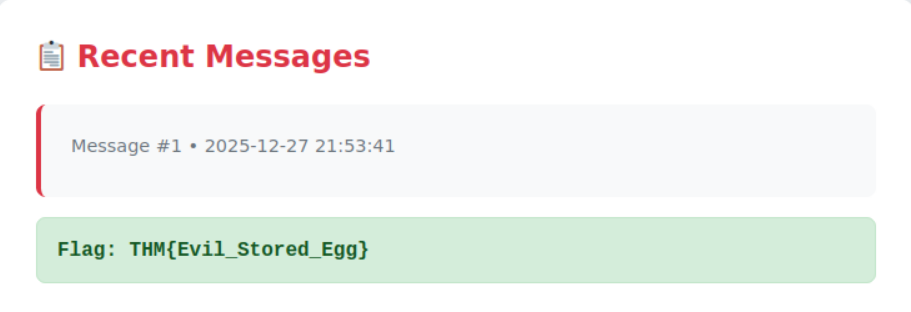
What’s the stored XSS flag?
For this one we will move on to the “message” field on the site, which takes in text and actually saves it on the backend, allowing us to exploit XSS on it. Using a simple payload such as <script>alert('TEXT HERE')</script> will reveal the flag.
Unlike Reflected XSS, Stored XSS is more dangerous because the malicious script is permanently saved in the application’s database. This means every user who views the affected page will automatically execute the attacker’s script without any additional interaction required. It’s a “set and forget” attack that can compromise multiple users over time.
Answer: THM{Evil_Stored_Egg}